Disclosure: The views and opinions expressed here belong entirely to the creator and manufacture no longer signify the views and opinions of crypto.news’ editorial.
Final November, DEX aggregator KyberSwap changed into as soon as hacked to the tune of $47 million, tanking its protocol and losing the funds of its liquidity suppliers. In a unfamiliar flip of events, the mysterious hacker made an unparalleled query to launch the stolen funds most efficient if the total govt workers stop and made him CEO. Unsurprisingly, this demand changed into as soon as rejected, and the hacker began bridging the stolen funds to Ethereum the utilization of the Synapse protocol.
KyberSwap barely survived the incident and changed into as soon as compelled to cut half of its workers throughout, as its total price locked dropped by 68 percent. As with all defi hacks, this one is miserable, but there could be a silver lining.
Beware of the bridge
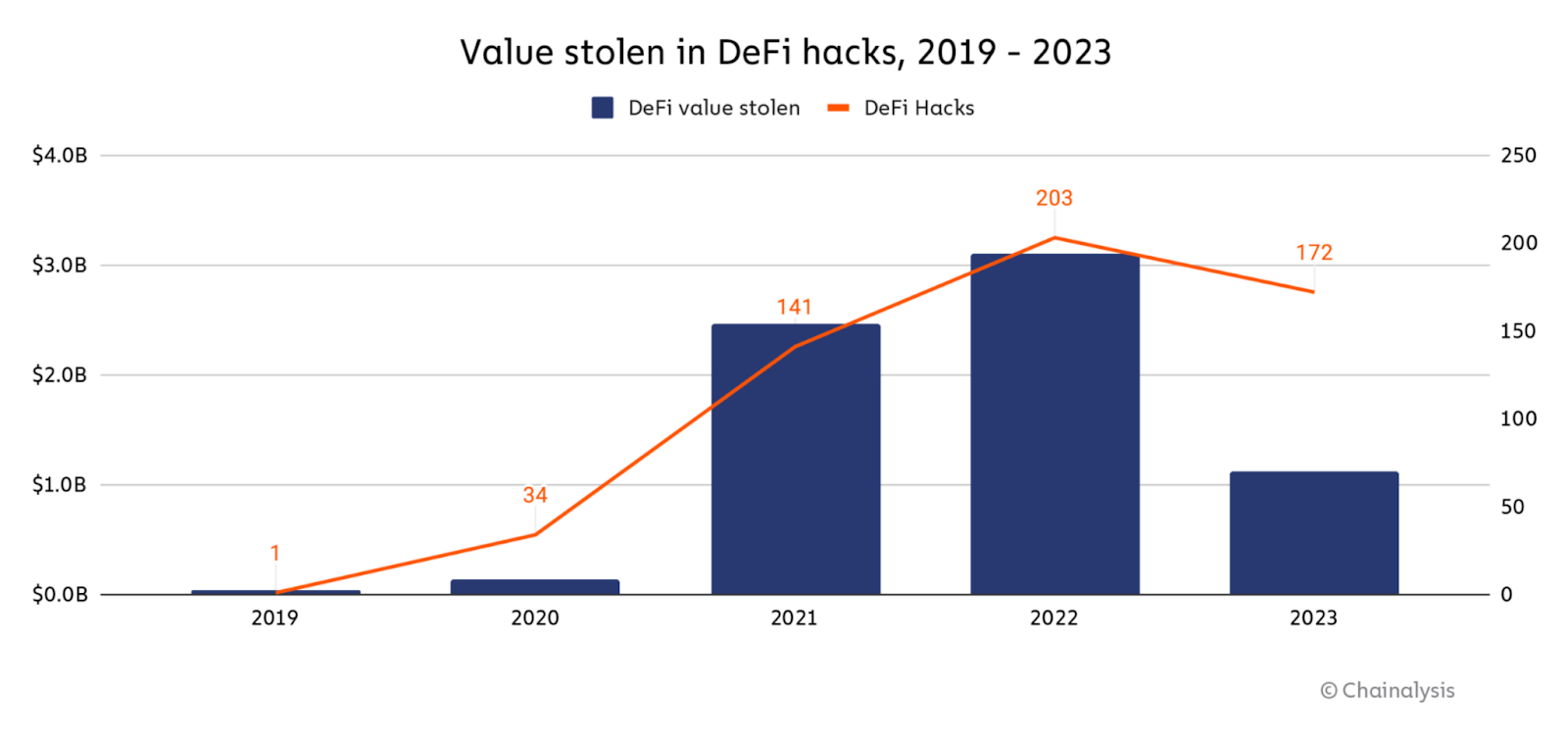
When put next to the early days of the crypto iciness, the price misplaced in defi hacks dropped by 64 percent in 2023, with the median loss per hack declining by 7.5 percent, according to Chainalysis data. And not utilizing a doubt, that is a particular pattern and a testament to the final pattern of the defi place and its growth in security. Bridges—blockchain protocols fostering infamous-chain interoperability—have contributed to defi’s expanded capabilities by unlocking isolated “islands” of liquidity, enabling sources to head with the circulation extra freely.
Bridges moreover stimulate innovation by enabling developers to search out new methods to build basically the most of infamous-chain capabilities. We will detect this thru the advent of new financial products, improved scalability, enhanced privateness capabilities, less complicated collaborative measures, and versatile danger administration.
Despite the decline in security breaches and the surge in bridge-based mostly defi innovation, blockchain interoperability is serene barely tiny. Moderately than fostering well-liked interoperability, every infamous-chain protocol or bridge represents a link between two blockchain networks, that device correct interoperability would require a posh web of diverse protocols linking every blockchain to at least one every other.
This affords its recognize place of security challenges. Despite the decline in hacks, the defi place is serene overrun by hackers probing for capability flaws in a protocol or a natty contract vulnerability to milk. Since most bridges depend upon natty contracts, that it’s seemingly you’ll presumably ask hackers to proceed testing them—be it a centralized alternate, layer-2 chain, or a place of oracles hosted by a third-occasion server.
Inherent security challenges, particularly on unregulated bridges, are almost about inconceivable to utterly do away with because most bridges have interaction with external systems, making them inclined to hacking or manipulation. Users transferring sources between disparate blockchain networks by strategy of a depended on or trustless bridge need to weigh serious security concerns.
On the total speaking, depended on bridges just like the Binance Bridge provide simplicity and compliance at the expense of centralization thru a third-occasion entity. Trustless bridges, on the assorted hand, prioritize decentralization, security, and permissionless access—but their reliance on natty contracts affords hackers with a clear assault vector.
Nonetheless, each and every forms of bridges can and had been exploited. Furthermore, the final lack of KYC and AML protocols amongst most bridges makes them a hacker’s most efficient buddy when needing to scrub stolen funds. Since bridges are the closest and most accessible mechanism to weeding out the boundaries between isolated blockchains, defi developers and customers must proceed with caution when the utilization of any infamous-chain protocol.
Why compliance matters
The resolution between trustless and depended on bridges comes appropriate down to the particular spend case, requirements, and commerce-offs that developers or customers prioritize or are prepared to rep. An moderate web3 user taking a examine to switch funds from one wallet to every other can even decide for a depended on bridge in consequence of its simplicity, flee, and lower fuel payments. Nonetheless, a dApp developer could prefer a trustless bridge to maintain complete administration over their sources internal a decentralized surroundings.
The safety part is often taken as a proper when trying to bridge sources. While each and every trustless and depended on bridges can adhere to a great deal of levels of compliance and danger mitigation—or discard it altogether—the utilization of a bridge that capabilities a sturdy compliance layer no doubt has its merits.
Let’s return to the KyberSwap hack to better perceive the imaginable implications of those security risks.
By analyzing the on-chain data, it’s obvious that had the Synapse protocol deployed a compliance layer, the hacker by no device would’ve been in a place to funnel the sources into an Ethereum-based mostly wallet and build a getaway. A danger-mitigation platform with an stop-to-stop compliance module can even be applied to any dApp or protocol and reject potentially problematic transactions equivalent to vigorous millions in stolen funds.
Likelihood mitigation isn’t a “bonus characteristic” that initiatives can sideline anymore. As regulatory our bodies mull extra complete laws, compliance will became ever extra principal, particularly as used financial institutions proceed flirting with offering defi services and products to their clientele.
It’s principal to uncover that at the side of a compliance layer to any decentralized protocol isn’t about censorship or opposing crypto’s core ethos of financial freedom and elimination of intermediaries. Moderately, it’s entirely about conserving user sources from being hijacked by criminals, alarm supporters, and more than just a few injurious actors.
As the crypto world strives for broader adoption, the necessity for compliance mechanisms is extra very principal than ever. With assault vectors in defi repeatedly evolving, hacks and thieves will proceed to threaten the integrity of the total industry and undermine the purpose of mainstream adoption.
While bridges don’t allow well-liked interoperability all the absolute most life like device thru the tall blockchain ecosystem, upright compliance can decrease risks for customers and developers, and safeguard defi’s growth. Therefore, developers could be luminous to part in a bridge’s compliance requirements when horny in infamous-chain transactions.
Man Vider is the co-founder and CTO of Kima, a decentralized, blockchain-based mostly cash switch protocol. Man’s background entails over two and a half of decades of pattern management with roles at Yahoo, ADP, BMC, Blue Inferior/Blue Defend, and Fisker Car. Additionally, Man has co-founded three startups and held consulting positions in deep-tech and web3 initiatives. Within the final few years, he honed his experience in fintech and blockchain. Man’s previous entrepreneurial endeavors encompass Amodello, the first home invent AR app in 2010, and ExPOS, an data analytics instrument for the hospitality industry in 2012.

