Suspected North Korean operatives are allegedly the usage of fallacious job applications to infiltrate web3 projects, siphoning off hundreds and hundreds and elevating security concerns.
In the last few years, blockchain and web3 had been at the forefront of technological innovation. Nonetheless, to paraphrase a quote, with gargantuan innovation comes gargantuan possibility.
Contemporary revelations comprise uncovered a posh method by operatives suspected to be affiliated with the Democratic Folks’s Republic of Korea to infiltrate the sector thru fallacious job applications, elevating alarms referring to the protection and integrity of the industry.
Table of Contents
Financial motives and cyber ideas
North Korea’s economy has been severely crippled by global sanctions, limiting its entry to significant sources, limiting exchange alternatives, and hindering its capability to comprise interplay in world financial transactions.
In response, the regime has employed diversified the staunch method to avoid these sanctions, including illicit shipping practices, smuggling, and tunneling, as effectively because the usage of front companies and foreign banks to conduct transactions somehow.
Nonetheless, considered one of many DPRK’s most unconventional ideas of elevating income is its reported exercise of a posh cybercrime battle program that allegedly conducts cyberattacks on financial institutions, crypto exchanges, and other targets.
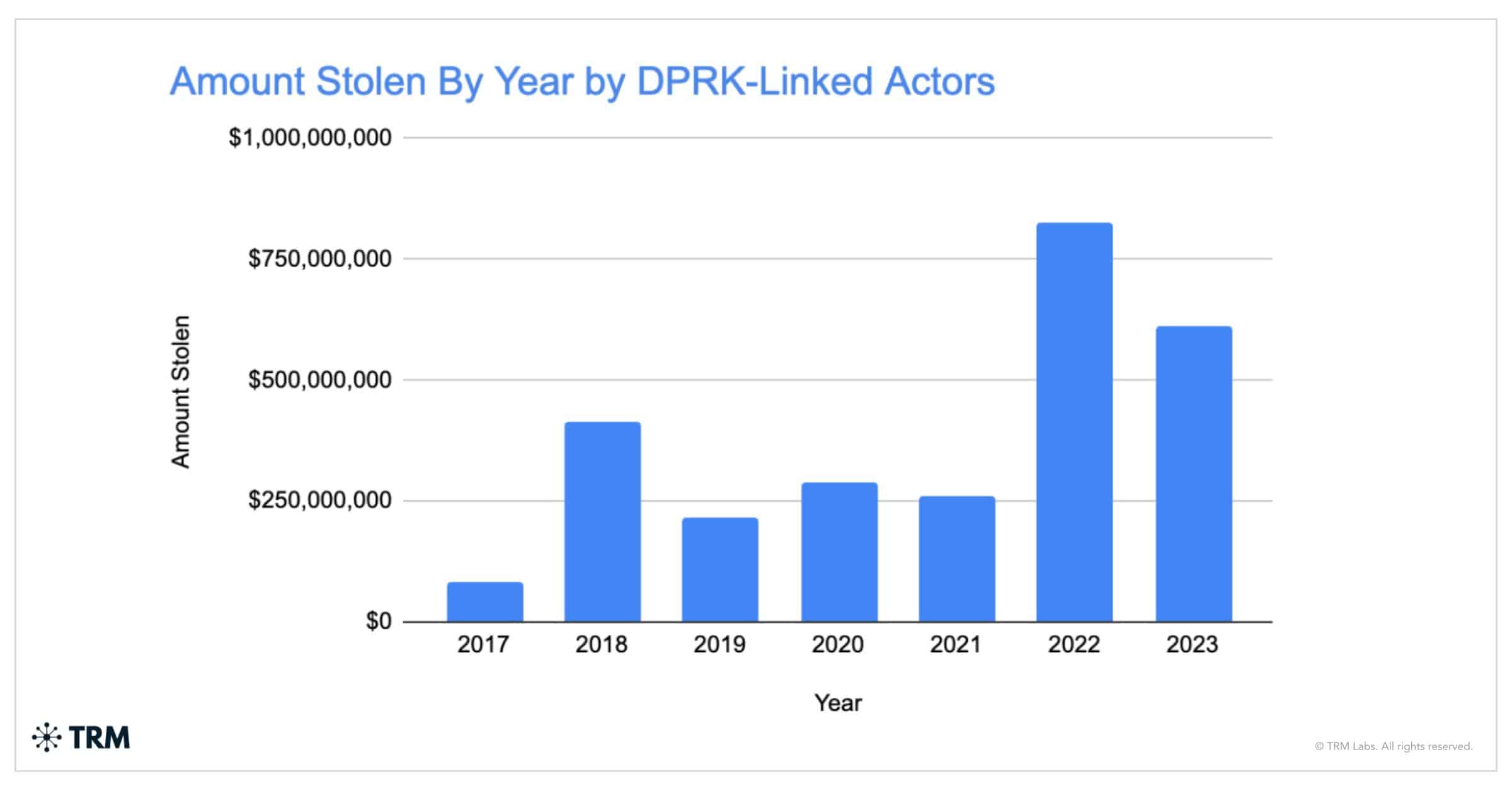
The crypto industry has been considered one of many greatest victims of this rogue narrate’s alleged cyber operations, with a TRM document from earlier in the 12 months indicating crypto lost at the least $600 million to North Korea in 2023 on my own.
In total, the document stated that North Korea turned into to blame for an glimpse-watering $3 billion worth of crypto stolen since 2017.
With crypto seemingly a soft and profitable aim, reviews comprise emerged of DPRK-linked actors tightening the screw by infiltrating the industry the usage of fallacious job applications.
Once employed, these operatives are in a better narrate to take and siphon off funds to strengthen North Korea’s nuclear weapons program and circumvent the realm financial restrictions imposed on it.
The modus operandi: fallacious job applications
Going by tales in the media and records from authorities companies, it appears to be DPRK operatives comprise perfected the art work of deception, crafting fallacious identities and resumes to stable a ways-off jobs in crypto and blockchain companies worldwide.
An Axios account from Might maybe maybe also 2024 highlighted how North Korean IT specialists were gaming American hiring practices to infiltrate the nation’s tech condo.
Axios stated the North Korean brokers exercise forged paperwork and fallacious identities, usually overlaying their gorgeous areas with VPNs. Furthermore, the account claimed that these would-be faulty actors essentially aim heavenly roles in the blockchain sector, including builders, IT specialists, and security analysts.
300 companies tormented by fallacious a ways-off job application rip-off
The dimension of this deception is immense, with the U.S. Justice Department lately revealing that better than 300 U.S. companies were duped into hiring North Koreans thru a extensive a ways-off work rip-off.
These scammers no longer handiest filled positions in the blockchain and web3 condo but additionally allegedly tried to penetrate extra stable and heavenly areas, including authorities companies.
In response to the Justice Department, the North Korean operatives historical stolen American identities to pose as home technology professionals, with the infiltration generating hundreds and hundreds of bucks in income for their beleaguered nation.
Curiously, considered one of many orchestrators of the method turned into an Arizona woman, Christina Marie Chapman, who allegedly facilitated the narrate of these workers by growing a network of so-known as “laptop farms” in the U.S.
These setups reportedly allowed the job scammers to appear as if they were working at some stage in the USA, thereby deceiving heaps of companies, including diverse Fortune 500 companies.
Notable incidents and investigations
Various high-profile circumstances comprise proven how these North Korea-linked brokers infiltrated the crypto industry, exploited vulnerabilities, and engaged in pretend activities.
Cybersecurity consultants esteem ZachXBT comprise equipped insights into these operations thru detailed analyses on social media. Below, we comprise a look at a few of them.
Case 1: Light Fury’s $300K switch
ZachXBT lately spotlighted an incident spirited an alleged North Korean IT employee the usage of the alias “Light Fury.” Working below the fallacious name Gary Lee, ZachXBT claimed Light Fury transferred over $300,000 from his public Ethereum Title Carrier (ENS) handle, lightfury.eth, to Kim Sang Man, a name which is on the Space of job of Foreign Resources Adjust (OFAC) sanctions listing.
DPRK IT workers are in overall easy to narrate and are no longer the smartest folk.
Example: Light Fury (@lee_chienhui) is a DPRK IT employee who transferred $300K+ from his public ENS handle to Kim Sang Man who’s on the OFAC sanctions listing.
Fake Title: Gary Lee
Alias: Light… https://t.co/2PlGnpYBFi pic.twitter.com/K1Xnd4oPSY— ZachXBT (@zachxbt) July 15, 2024
Light Fury’s digital footprint entails a GitHub fable, which presentations him as a senior dapper contract engineer who has made better than 120 contributions to a mode of projects in 2024 on my own.
Case 2: the Munchables hack
The Munchables hack from March 2024 serves as some other case look showing the importance of thorough vetting and background assessments for key positions in crypto projects.
This incident intriguing the hiring of four builders, suspected to be the equivalent particular person from North Korea, who were tasked with growing the project’s dapper contracts.
The fallacious group of workers turned into linked to the $62.5 million hack of the GameFi project hosted on the Blast layer-2 network.
Example 2: Four other DPRK IT workers who were on the Munchables group of workers and desirous referring to the $62.5M hack https://t.co/NqoHZwiSkT
— ZachXBT (@zachxbt) July 15, 2024
The operatives, with GitHub usernames similar to NelsonMurua913, Werewolves0493, BrightDragon0719, and Super1114, it appears to be displayed coordinated efforts by recommending each other for jobs, transferring payments to the equivalent alternate deposit addresses, and funding each other’s wallets.
Furthermore, ZachXBT stated they usually historical an identical price addresses and alternate deposit addresses, which indicated a tightly-knit operation.
The theft came about because Munchables at the delivery historical an upgradeable proxy contract that turned into managed by the suspected North Koreans who had inveigled themselves into the group of workers, quite than the Munchables contract itself.
This setup equipped the infiltrators with significant administration over the project’s dapper contract. They exploited this administration to manipulate the dapper contract to construct themselves a balance of 1 million Ethereum.
Regardless that the contract turned into later upgraded to a extra stable version, the storage slots manipulated by the alleged North Korean operatives remained unchanged.
They reportedly waited except satisfactory ETH had been deposited in the contract to win their attack beneficial. When the time turned into factual, they transferred approximately $62.5 million worth of ETH into their wallets.
Fortunately, the account had a overjoyed ending. After investigations revealed the everyday builders’ roles in the hack, the leisure of the Munchables group of workers engaged them in intense negotiations, following which the faulty actors agreed to return the stolen funds.
$97m has been secured in a multisig by Blast core contributors. Took a fascinating occupy the background but I’m grateful the ex munchables dev opted to return all funds in the pause with out any ransom required. @_munchables_ and protocols integrating with it esteem @juice_finance…
— Pacman | Blur + Blast (@PacmanBlur) March 27, 2024
Case 3: Holy Pengy’s adverse governance attacks
Governance attacks comprise additionally been a tactic employed by these fallacious job candidates. One such alleged perpetrator is Holy Pengy. ZachXBT claims that name is an alias for Alex Chon, an infiltrator allied to the DPRK.
When a community member alerted users a pair of governance attack on the Indexed Finance treasury, which held $36,000 in DAI and approximately $48,000 in NDX, ZachXBT linked the attack to Chon.
On-chain is where things win appealing.
The actual person unhurried the Indexed Finance governance attack additionally tried one on @relevantfeed thru 0x9b9 earlier this month.
0x9b9 turned into funded by Alex Chon an alleged DPRK IT employee who has been fired from at the least 2 roles for suspicious… https://t.co/vXYAmzPxnn pic.twitter.com/nXoVDaWYvZ
— ZachXBT (@zachxbt) November 18, 2023
In response to the on-chain investigator, Chon, whose GitHub profile components a Fat Penguins avatar, steadily modified his username and had been reportedly fired from at the least two diversified positions for suspicious habits.
In an earlier message to ZachXBT, Chon, below the Pengy alias, described himself as a senior fleshy-stack engineer that specialise in frontend and solidity. He claimed he turned into interested by ZachXBT’s project and desired to hitch his group of workers.
An handle linked to him turned into identified as being unhurried each the Indexed Finance governance attack and an earlier one towards Related, a web3 records sharing and discussion platform.
Case 4: Suspicious project in Starlay Finance
In February 2024, Starlay Finance faced a prime security breach impacting its liquidity pool on the Acala Community. This incident ended in unauthorized withdrawals, sparking significant scenario at some stage in the crypto community.
The lending platform attributed the breach to “irregular habits” in its liquidity index.
Safety Incident Document: Anomaly in USDC Pool and Exploitation
Executive Summary:
This document major components a prime security incident at some stage in the Starlay protocol’s USDC lending pool on the Acala EVM platform. An exploit turned into identified and executed attributable to irregular habits in the… https://t.co/8Q3od5g6Rc— Starlay Finance🚀 (@starlay_fi) February 9, 2024
Nonetheless, following the exploit, a crypto analyst the usage of the X handle @McBiblets, raised concerns concerning the Starlay Finance building group of workers.
I’ve regarded into the @starlay_fi incident and there is something extraordinarily suspicious about their dev group of workers, David and Kevin
I’d no longer be stunned in the occasion that they were to blame for basically the most in vogue attack and my instinct is making me contemplate they’d perchance also fair be DPRK affiliated
Right here is why 🧵
— McBiblets (@mcbiblets) March 16, 2024
As may perchance perchance be considered in the X thread above, McBiblets turned into notably intriguing about two folk, “David” and “Kevin.” The analyst uncovered odd patterns in their activities and contributions to the project’s GitHub.
In response to them, David, the usage of the alias Wolfwarrier14, and Kevin, identified as devstar, regarded as if it would section connections with other GitHub accounts esteem silverstargh and TopDevBeast53.
As such, McBiblets concluded that these similarities, coupled with the Treasury Department’s warnings about DPRK-affiliated workers, beneficial the Starley Finance job may perchance perchance presumably also fair had been a coordinated effort by a minute community of North Korean linked infiltrators to make the most of the crypto project.
Implications for the blockchain and web3 sector
The seeming proliferation of suspected DPRK brokers in key jobs poses significant dangers to the blockchain and web3 sector. These dangers are no longer factual financial but additionally win attainable records breaches, mental property theft, and sabotage.
For occasion, operatives may perchance perchance presumably also potentially implant malicious code within blockchain projects, compromising the protection and functionality of complete networks.
Crypto companies now face the scenario of rebuilding trust and credibility in their hiring processes. The financial implications are additionally excessive, with projects potentially losing hundreds and hundreds to pretend activities.
Furthermore, the U.S. authorities has indicated that funds funneled thru these operations usually pause up supporting North Korea’s nuclear ambitions, extra complicating the geopolitical panorama.
For that reason, the community must prioritize stringent vetting processes and better safety features to safeguard towards such counterfeit job-hunting ideas.
It’s miles serious for there to be enhanced vigilance and collaboration across the sector to thwart these malicious activities and offer protection to the integrity of the burgeoning blockchain and crypto ecosystem.

