North Korean recount-backed hackers, the Lazarus Community, basically employed spear phishing assaults to raise funds over the closing year, with the neighborhood receiving presumably the most mentions in submit-hack analyses over the closing one year, basically based mostly totally on South Korean cybersecurity company AhnLab.
Spear phishing is one among presumably the most neatly-preferred programs of assault by corrupt actors treasure Lazarus, using spurious emails, “disguised as lecture invites or interview requests,” AhnLab analysts mentioned within the Nov. 26, 2025, Cyber Risk Traits & 2026 Security Outlook memoir.
The Lazarus Community is the first suspect within the back of many assaults all over many sectors, in conjunction with crypto, with the hackers suspected to be responsible for the $1.4 billion Bybit hack on Feb. 21 and the more most neatly-liked $30 million exploit of the South Korean crypto replace Upbit on Thursday.
Solutions to offer protection to your self from spear phishing
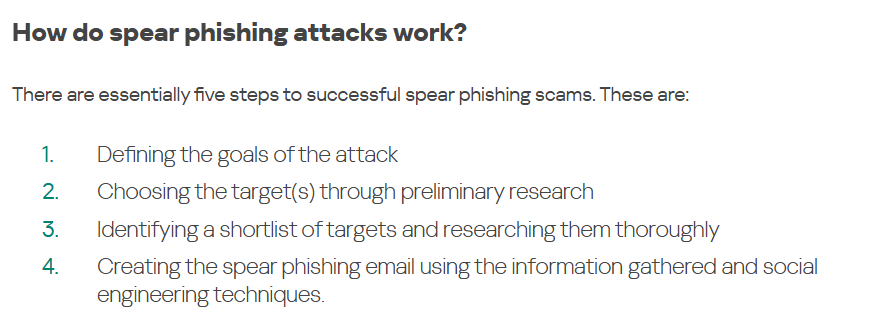
Spear phishing assaults are a focused develop of phishing the build hackers study their supposed purpose to dangle files and masquerade as a trusted sender, thereby stealing a sufferer’s credentials, installing malware, or having rep admission to to sensitive programs.
Cybersecurity agency Kaspersky recommends the next programs to offer protection to against spear phishing: using a VPN to encrypt all online exercise, avoiding the sharing of excessive deepest particulars online, verifying the source of an electronic mail or conversation by an different channel, and, the build imaginable, enabling multifactor or biometric authentication.
‘Multi-layered defense’ wished to fight corrupt actors
The Lazarus Community has focused the crypto residence, finance, IT and defense, basically based mostly totally on AhnLab, and changed into once additionally presumably the most ceaselessly mentioned neighborhood in after-hack evaluation between October 2024 and September 2025 this year, with 31 disclosures.
Fellow North Korean-linked hacker outfit Kimsuky changed into once next with 27 disclosures, adopted by TA-RedAnt with 17.
AhnLab mentioned a “multi-layered defense system is valuable” for firms hoping to curb assaults, similar to customary security audits, maintaining software program up to this point with presumably the most neatly-liked patches and schooling for staff members on assorted assault vectors.
Connected: CZ’s Google story focused by ‘govt-backed’ hackers
In the period in-between, the cybersecurity company recommends individuals adopt multifactor authentication, withhold all security software program up to this point, steer sure of running unverified URLs and attachments, and handiest download train material from verified reliable channels.
AI will create corrupt actors more effective
Going into 2026, AhnLab warned that contemporary technologies, similar to artificial intelligence, will handiest create corrupt actors more environment friendly and their assaults more subtle.
Attackers are already capable of using AI to assemble phishing websites and emails which would be advanced to uncover aside with the naked see, AhnLab mentioned, however AI can “originate assorted modified codes to evade detection,” and create spear phishing more environment friendly by deepfakes.
“With presumably the most neatly-liked develop within the use of AI models, deepfake assaults, similar to these that raise urged files, are expected to conform to a level that makes it advanced for victims to title them. Particular attention may perchance be required to forestall leaks and to secure files to forestall them.”
Journal: 2026 is the year of pragmatic privacy in crypto: Canton, Zcash and more

